Ever feel the pain of constantly copying and pasting short-lived AWS credentials? It’s time-consuming, error-prone, and frankly, annoying. But fear not, there’s a better way! This guide will show you how to set up AWS Single Sign-On (SSO), a magical tool that lets you access your AWS accounts with just a single login, saving you precious time and frustration.
The Struggle is Real:
Many engineers in companies using AWS Organizations face the same struggle: managing complex credential setups. They spend their valuable time copying and pasting short-term keys, which is tedious and can lead to mistakes. But worry no more! We’re here to break free from the shackles of manual credential management.
Quick Context
Your company is using AWS organizations and they give you a sign-in URL that might look something like https://d-xxxxxx.awsapps.com/start/#/
You follow the prompts and land on a page with one or more accounts, for example like that:
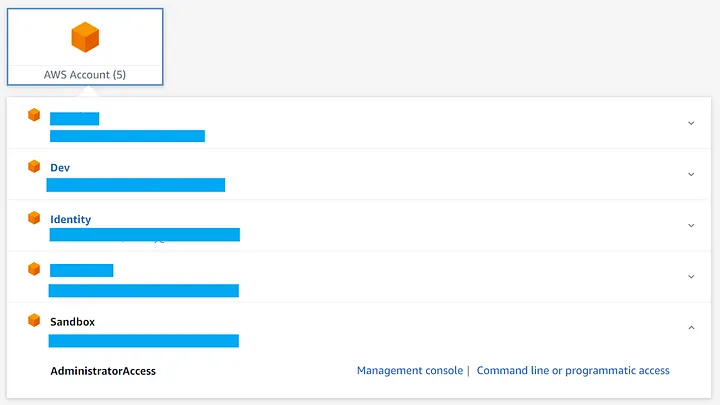
Then you can pick a AWS account and a role, and choose to go to the Web UI or click the Command line link for instructions.
The hard way
When clicking on the Command line link, this window opens:
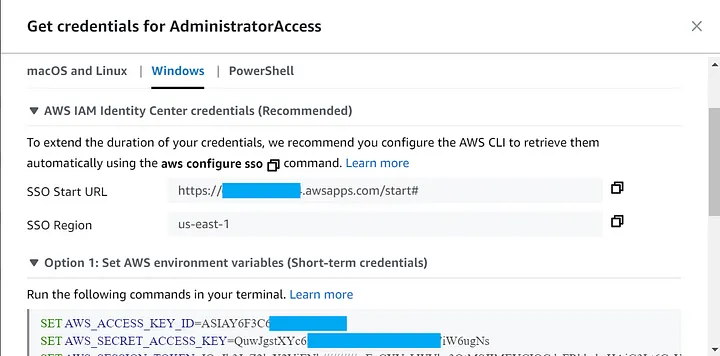
Most people familiar with AWS will immediately recognize the familiar environment variables and go to Option 1, cause it says Option 1, and paste that in their terminal and voila, access granted.
A few hours later, they realize the credentials have expired, go back to that screen, copy the new set of keys and move on.
The next day, they need to run some commands in another account. A lot of engineers will just go back to that screen, copy the new set of keys and so on, day after day.
One thing is for certain, nobody likes doing that…
The Hero Arrives: AWS Configure SSO
Meet your new best friend – aws configure sso. This powerful command, run in your terminal, is the key to unlocking the power of SSO. Let’s see how it works:
Step 1: Ditch the Copy-Pasting:
Forget the “Command line link” in the AWS SSO console; it leads you down the path of manual key management. Instead, type aws configure sso in your terminal. This command sets up a “named profile” for your AWS account, like a personal key that remembers your login information.
Step 2: Name it Right:
Don’t settle for the generic profile name. Give it a meaningful label like “sandbox-admin” or “qa” for easy identification. This will make switching between accounts a breeze!
C:\>aws configure sso
SSO session name (Recommended): thynkbetter
Attempting to automatically open the SSO authorization page in your default browser.
If the browser does not open or you wish to use a different device to authorize this request, open the following URL:
https://device.sso.us-east-1.amazonaws.com/
Then enter the code:
JCBR-LFGN
There are 5 AWS accounts available to you.
Using the account ID 1143426556690
The only role available to you is: AdministratorAccess
Using the role name "AdministratorAccess"
CLI default client Region [None]: us-east-1
CLI default output format [None]: json
CLI profile name [AdministratorAccess-1143426556690]: sandbox
Step 3: Remember Me (Optional):
Typing --profile every time you want to use your saved profile can get old. To avoid this, set an environment variable:
- Linux/macOS:
export AWS_PROFILE=your-profile-name - Windows:
set AWS_PROFILE=your-profile-name
Now, simply typing aws s3 ls will use the saved profile, and you’re good to go!
Bonus Tip:
After logging out, simply run aws sso login and set AWS_PROFILE again to regain access. No need to re-run the entire configuration!
Level Up: Advanced Techniques (Optional)
For the extra-savvy users, here are some optional tips to take your SSO experience to the next level:
- One Organization, One Profile: If you only have one AWS organization, you can skip specifying the session name during configuration.
- Default Profile: Choose one of these options to avoid setting the profile every time:
- Global Environment Variable: Set
AWS_PROFILEglobally for all commands. - Configuration File: Edit
~/.aws/configto set default SSO settings.
- Global Environment Variable: Set
- Multiple Profiles: Need access to different roles or accounts within the same organization? Use
aws configure sso existing sessioncommands to create dedicated profiles for each. - Multiple Organizations (Rare): If you’re lucky enough to have multiple organizations,
aws configure sso --sso-session myotherorgallows you to switch between them seamlessly.
Remember:
- Setting the profile environment variable is crucial to avoid confusing errors.
- In
~/.aws/config, edit only thedefaultsection, not[profile default].
The Grand Finale: Become a Master of SSO!
By following these simple steps, you’ve unlocked the power of AWS Single Sign-On. No more copy-pasting, no more wasted time! You can now efficiently and securely access your AWS accounts, focusing on what truly matters – your amazing projects. Share this knowledge with your colleagues and empower them to join the SSO revolution!
